p0f is a tool that can identify the operating system of a target host simply by examining captured packets even when the device in question is behind a packet firewall. P0f does not generate any additional network traffic, direct or indirect; no name lookups; no mysterious probes; no ARIN queries; nothing. In the hands of advanced users, P0f can detect firewall presence, NAT use, and existence of load balancers.
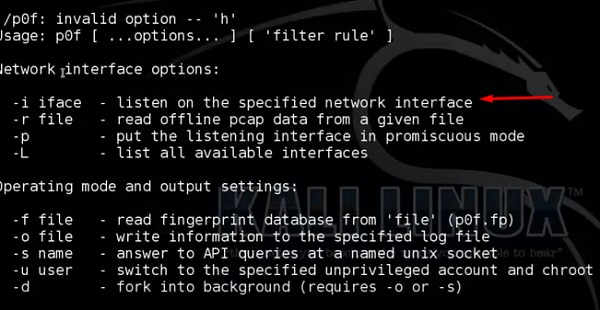
Type “p0f – h” in the terminal to see how to use it and you will get the following results.
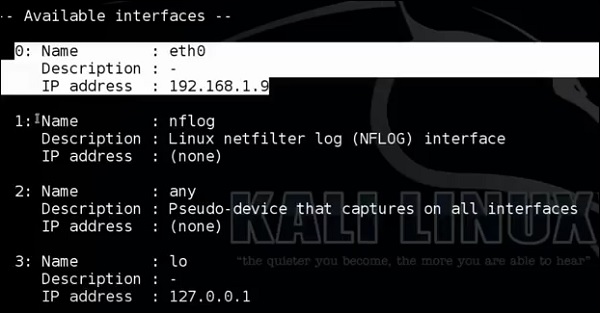
It will list even the available interfaces.
Then, type the following command: “p0f –i eth0 –p -o filename”.
Where the parameter "-i" is the interface name as shown above. "-p" means it is in promiscuous mode. "-o" means the output will be saved in a file.
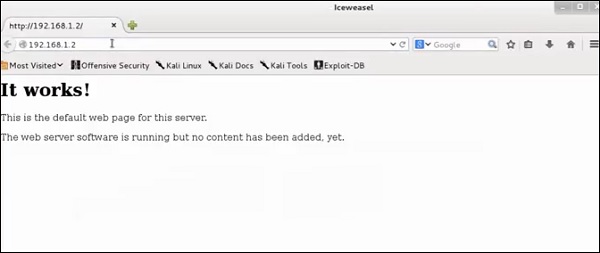
Open a webpage with the address 192.168.1.2
From the results, you can observe that the Webserver is using apache 2.x and the OS is Debian.







COMMENTS